Healthcare organizations face constant pressure to protect data and keep up with evolving security regulations. Yet many still rely on siloed tools, inconsistent processes, and limited resources—leaving them vulnerable to breaches, fines, and reputational harm. Health Catalyst helps security leaders go beyond checklists and manual work by unifying risk visibility, automating assessments, and simplifying reporting. With our solutions, organizations can manage cybersecurity more efficiently and show strong compliance across HIPAA, HITRUST, NIST, and other frameworks.
We help leaders solve questions like:
Break down silos and unify visibility across your internal systems, vendors, and security programs.
Result: A cohesive view of risk that supports smarter action.

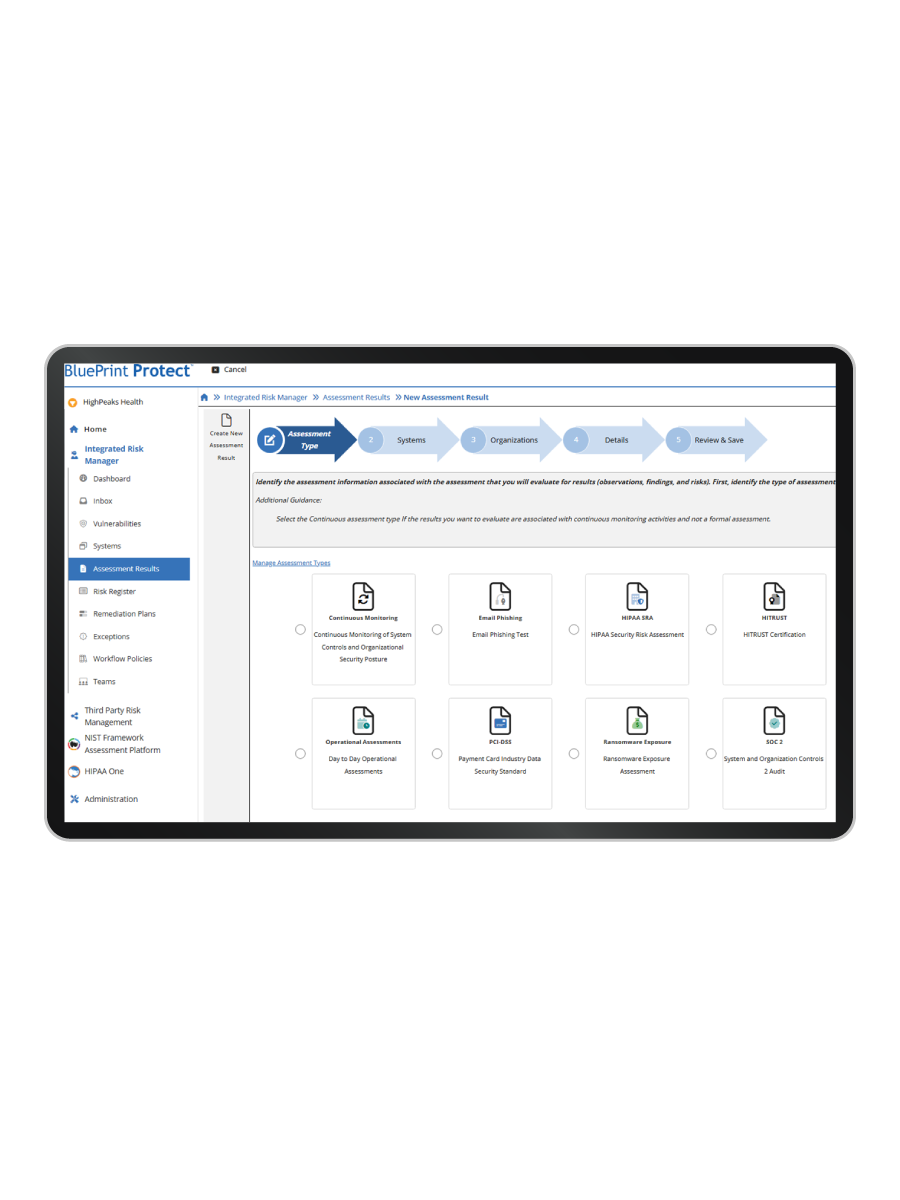
Go beyond the audit. Establish a sustainable security culture aligned to best practices and future growth.
Result: A future-ready foundation for cybersecurity and compliance.
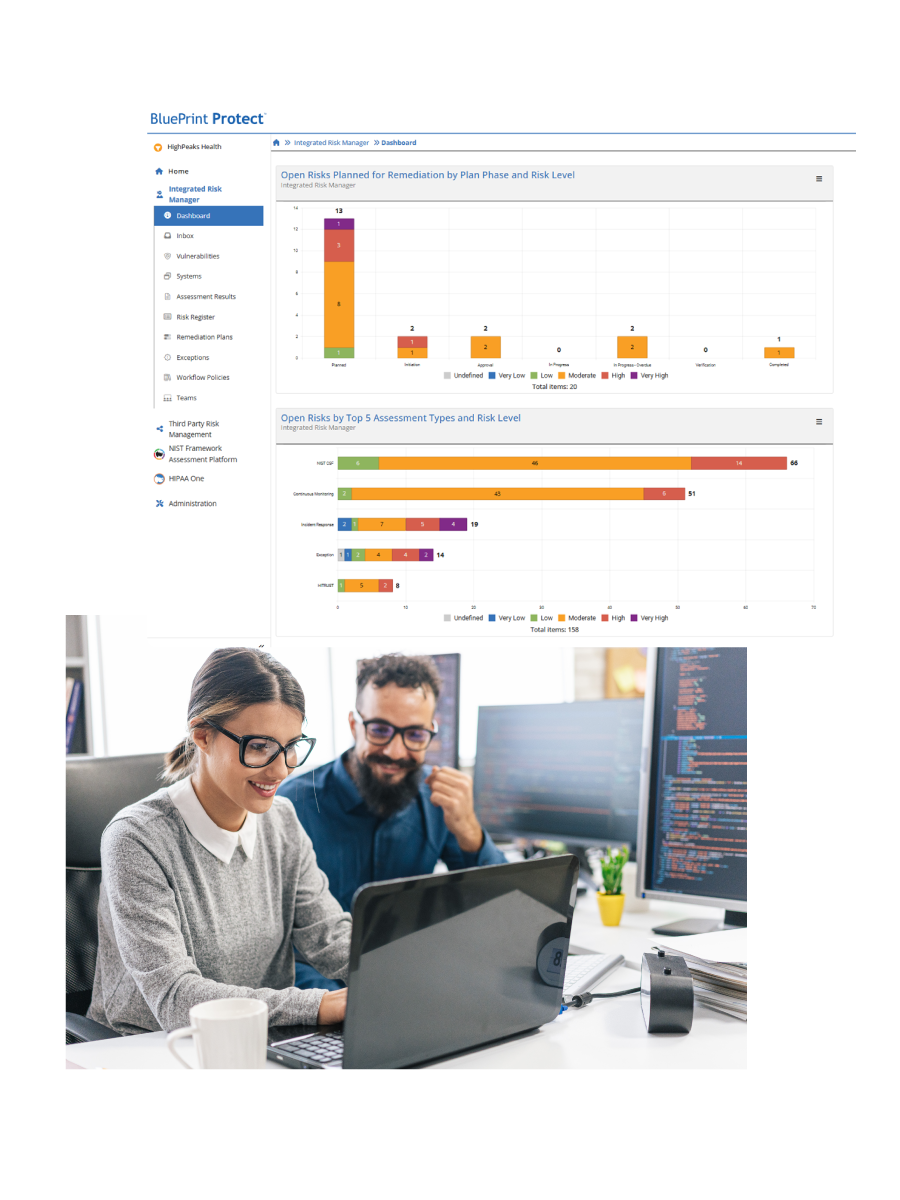
Streamline assessments, evidence collection, and compliance workflows to save time and reduce burnout.
Result: Fewer hours, stronger oversight, faster progress.
With Health Catalyst, you don’t just meet requirements—you build trust and resilience. Integrated tools, managed services, and advisory expertise help you stay ahead of risks and demonstrate your commitment to safeguarding patient information.
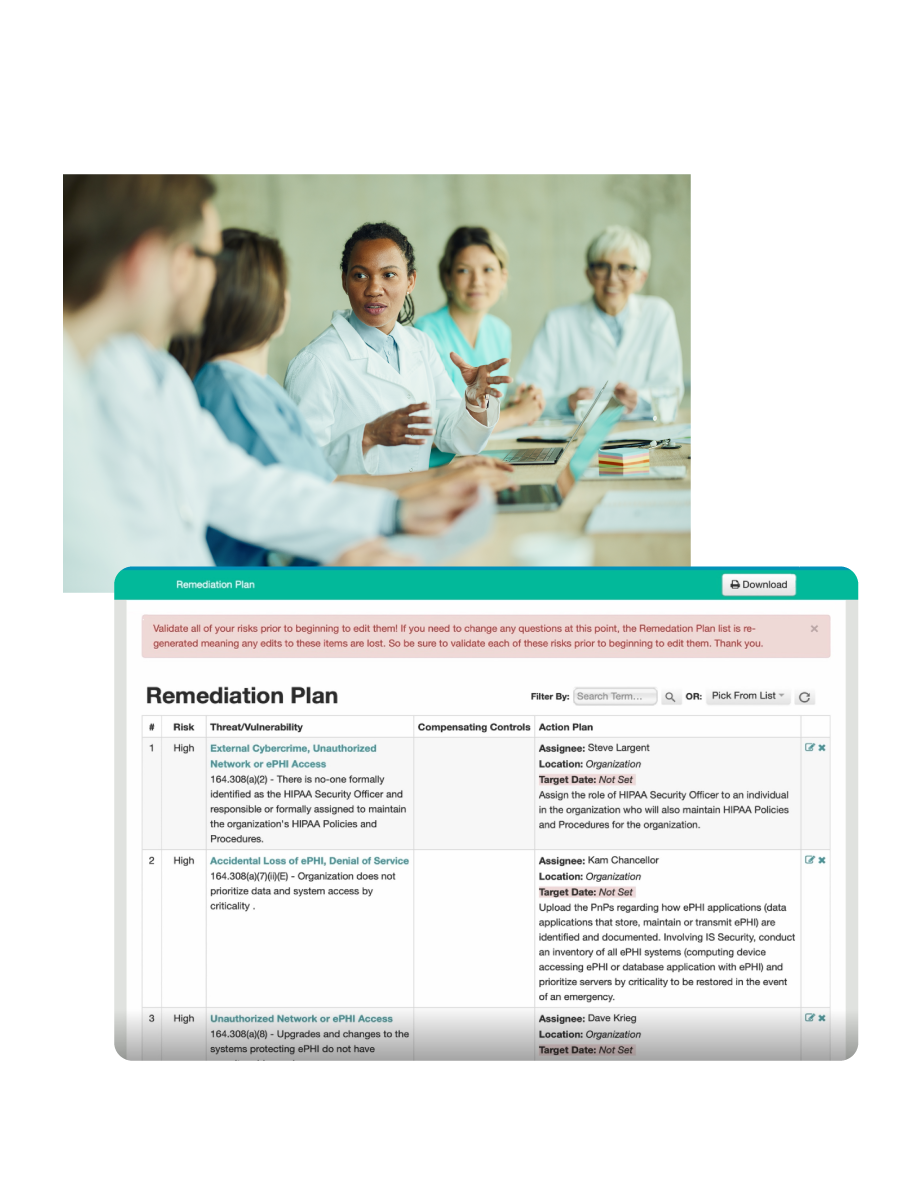
Keep staff aligned and accountable with clear tools, timely training, and shared visibility.
Result: A security-aware workforce focused on what matters most.
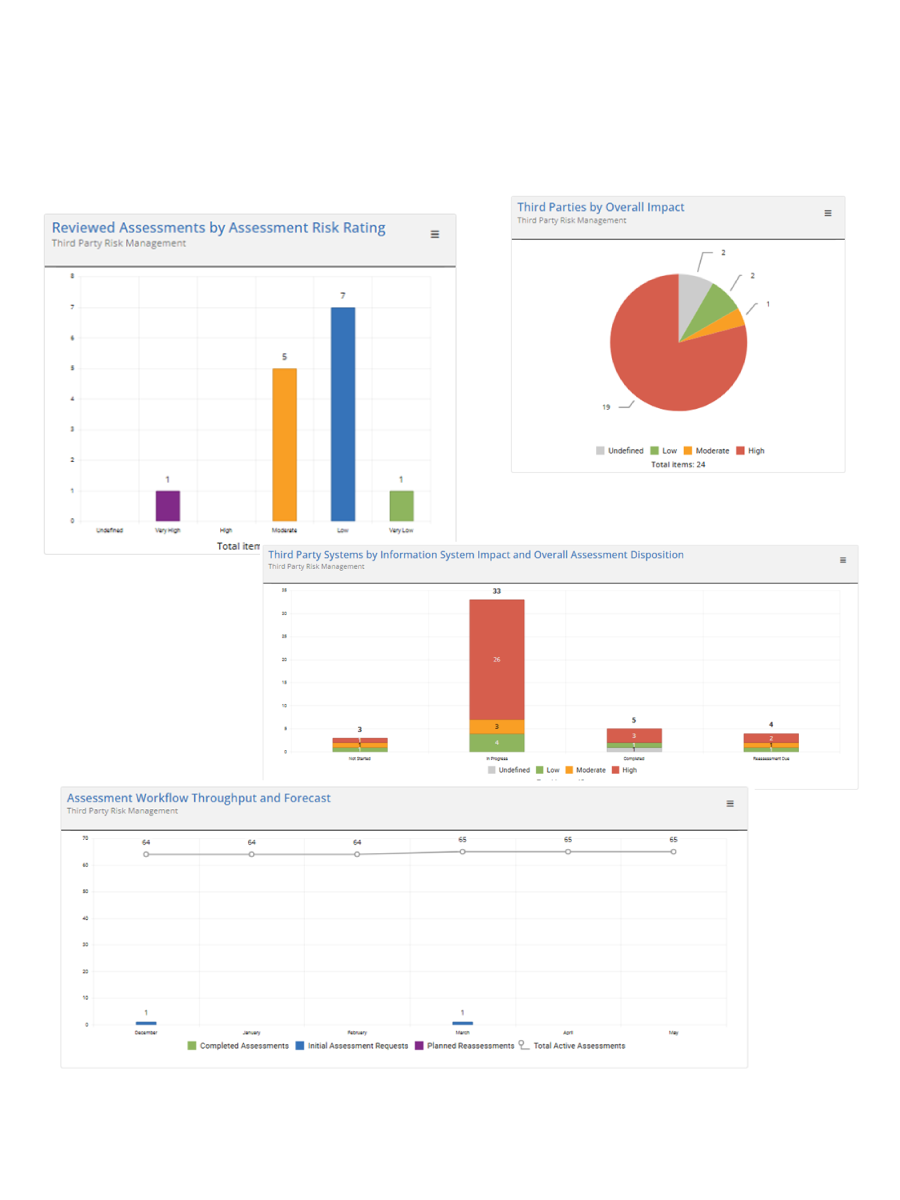
Skip the scramble. Automate compliance reporting and present clear insights to regulators and leadership.
Result: Less time compiling. More time protecting.




